Blog
Cyber Security Controls: Now Critical for Your Cyber Insurance Renewal
In the last few years, a common question for cyber insurance brokers has been “If I implement this cyber security control, will I get a discount on my cyber insurance premium?” In the past, the typical answer was “no.” However, these days, the answer has changed to “no, you won’t get a premium discount. But if you don’t implement that security control, you might not even get insurance.”

Security Controls: A Hard Turn for the Cyber Market
This increased scrutiny of specific cyber security controls is just one element of the hardening cyber insurance market. Pricing is up, terms are being restricted, and traditional hard-market components of insurance programs—such as co-insurance—are being implemented across the cyber insurance landscape.
AIG announced a revamped approach to the cyber market, introducing a sub-limit at 50% of the limit for any cyber event in which a ransom is demanded. They’ve also introduced co-insurance to the cyber market, requiring their clients to contribute 50% to any ransomware loss.
Other carriers have followed with similar approaches: adding ransomware sub-limits, co-insurance, or exclusions around the recent SolarWinds security breach, or limiting their appetite to small business only.
What’s the main culprit for all of these changes? It’s ransomware.
Increasing Frequency and Severity of Losses
Ransomware might seem like the only type of security incident you hear about these days, but that's for good reason. The impact on companies of every industry and size has been profound. According to Coveware, a ransomware negotiation and response firm, the average ransom payment increased from an average of $84,116 in the fourth quarter of 2019 to an average of $154,108 in Q4 2020—an 83% jump in just one year.
Insurance carriers have seen similar trends, with cyber insurance leader Beazley reporting that the total cost of ransom payments doubled from the first half of 2019 to the first half of 2020.
When you look at the specifics of cyber insurance coverage, it’s easy to see how the tactics of modern-day cyber criminals are influencing these loss trends. As detailed in our Cyber 101 blog post, the primary insuring agreement that responds to a ransomware event will be the cyber extortion coverage. This insuring agreement covers the actual ransom payment to an attacker and can also include any related computer forensics and legal expenses incurred by the victim company.
But today’s cyber criminals are unsatisfied with just encrypting a victim’s network and demanding a ransom payment. Coveware reports that in the fourth quarter of 2020, 70% of ransomware cases included an element of data exfiltration. For many companies, this data exfiltration can include personally identifiable information of consumers, triggering another element of a cyber insurance policy—the data breach insuring agreement.
The costs associated with a ransom demand and potential data breach haven’t even touched on the most expensive part of a ransomware event—the business downtime while network access is encrypted. Coveware’s fourth quarter report shows an average downtime of 21 days—a shocking aspect of ransomware for many victims.
This downtime can engage the business interruption elements of a cyber insurance policy, replacing lost profits and continuing operating expenses such as payroll during the downtime.
When you factor in all three of these cyber insurance coverage elements affected by a single security event such as ransomware, it becomes clear why insurance carriers are taking such drastic steps to curb their exposure to ransomware losses.
Cyber Security Controls in the Crosshairs
The changes happening in the cyber insurance market are not limited to price increases and coverage restrictions, however. Cyber insurance carriers are now asking much more pointed questions regarding what specific cyber security controls prospective customers have in place.
Nearly all cyber insurance carriers now require a supplemental application that includes questions on security and process controls which would prevent or at least minimize the impact and cost of a ransomware attack.
In analyzing these supplemental ransomware applications, some key characteristics emerge. Many of the processes and security tools implemented by clients fit into three categories: minimum required controls, baseline controls, and best practices.
[caption id="attachment_28709" align="alignnone" width="1024"]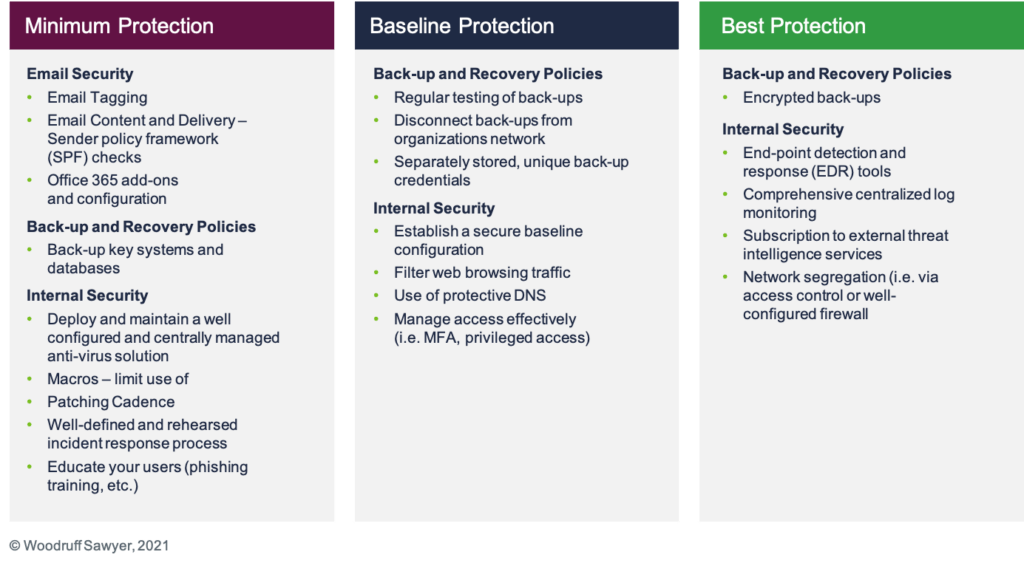 The level of sophistication required to qualify for insurance is increasing.[/caption]
The level of sophistication required to qualify for insurance is increasing.[/caption]
Many carriers will now decline to offer terms for companies that do not meet the minimum or sometimes even the baseline protection highlighted above. Additionally, underwriters are focused on strong answers to multi-factor authentication (MFA) controls, end-point detection and response tools, and segregation of backups.
Furthermore, the carriers are no longer simply taking your word for having some of the technical controls in place. Most cyber insurance carriers now perform external scans of a prospective customer’s network both to confirm you have specific controls in place and to identify any known vulnerabilities present on your network.
Plan to Be More Involved
With the drastic changes in the cyber insurance marketplace at the start of this year, the best course of action for a company to take is to plan for more engagement in advance of their cyber insurance renewal. Companies need to be prepared to share a large amount of data on their exposures, such as revenues or PII data volumes, as well as the controls they have in place to prevent or mitigate a cyber event.
And for the best results, be ready to start the renewal process early. Work with your broker to prepare comprehensive submission materials, highlighting your investments in cybersecurity and how you improved your processes from the prior year.
Just like having baseline protections in place through cyber security controls, this advance planning may be the only way to ensure you can qualify for insurance at all.
Author
Table of Contents












