Blog
Data Theft After Layoffs: Preventive Steps & the Insurance Response
Many prominent tech companies have recently conducted mass layoffs—some as a response to the slowing economy, and others to correct for pandemic hiring sprees.

Whatever the reason, one of the risks that arise when laying off employees is data theft, also known as data leakage and exfiltration. This can cause a company to lose out on business, lose its intellectual property, and suffer reputational damage.
Unfortunately, it's not uncommon, especially around the time of their departure, whether that departure is voluntarily or via a layoff or firing. A report from Cyberhaven, a software company focusing on securing data, shows a 23.1% increase in data exfiltration from employees the day before they were fired and a 109.3% increase the day they were fired.
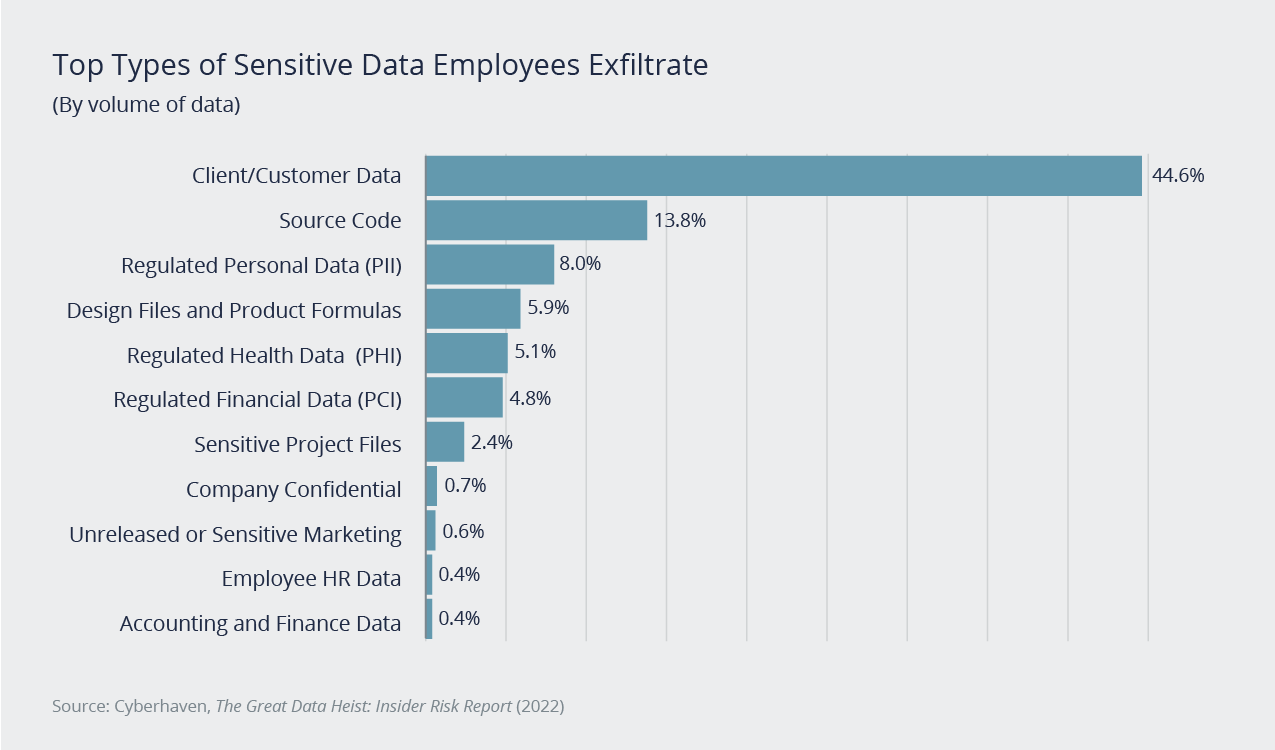
There are various steps to take to prevent or reduce data theft when you're preparing for layoffs. We'll discuss steps you can take to control your risk and the instances when a cyber insurance policy will (and won't) respond.
Risk and How It Arises
The knowledge of an impending layoff increases a company's risk of data theft. There are various ways it can happen. Human Resources may allow an employee to keep their laptop, and it doesn’t get wiped correctly. Perhaps a disgruntled employee steals data on their way out or feels the information would give them an advantage in searching for a new job. If the employee is in IT, they could leave a back door into the network that allows them entry once they're no longer employed.
Security Protocols to Control Risk
It's important to understand the risk mitigation tools that you can use and how cyber security controls come into play to help protect the company. Here are a few steps to take:
- Control your asset inventory. Understand what devices the company owns that can access the internal network, know which ones employees will be allowed to keep, and utilize a strong tracking system. As assets turn over during hirings and layoffs, make sure you have good insights into what assets remain.
- Implement strong identity management controls. This includes privileged account management and an up-to-date directory. Specialized tools can also give companies a good line of sight into who is accessing the network and an inventory of all the devices that should be connecting to the network, while blocking devices that aren't allowed. The company should also ensure that, as layoffs occur, people's access is turned off as quickly as possible.
- Review HR policies and procedures. The policy should state that the company can remotely wipe mobile devices under a bring-your-own-device policy and also state where your data is allowed to be stored. For example, employees shouldn't send company information through their personal email. These policies become important during layoffs, because you need to have the ability to wipe all your data off devices and close off access points immediately.
Data loss prevention (DLP) tools can tell you where data is traveling out of your network. If an employee sends data from their work email to their personal email, you may be able to intercept it. If there's a massive data flow that goes out in the middle of the night, right before layoffs happen, it's a red flag that DLPs can help with.
What to Do After IT and Risk Team Layoffs
The IT and risk management teams help you ensure strong cybersecurity controls and manage your cyber risk. That also means they have the most knowledge about how to handle incidents.
If your layoffs will affect these employees, review your incident response plan beforehand and make sure it still fits its purpose. Ensure that all the key people who are involved with the response plan are still employees at the company and that the incident response plan is still appropriate for your current business needs.
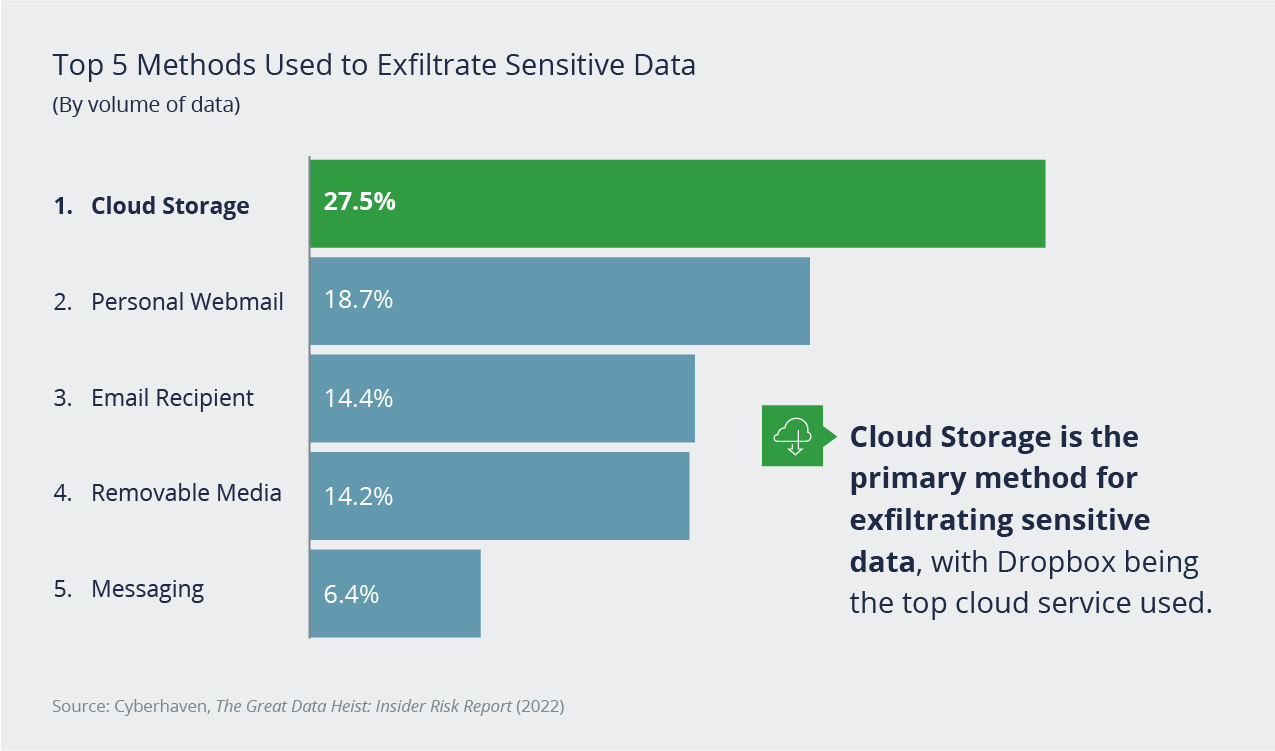
Cyber Insurance for Data Theft: What's Covered and What's Not
Despite strong controls, there's still risk. The good news is that a cyber insurance policy can support companies in certain areas.
Any sort of data breach or security breach that happens after a layoff, such as from a disgruntled employee, is covered under your cyber liability policy. This includes costs and expenses incurred responding to the data breach: from consumer notification costs to extortion amounts demanded by the employee, to cyber forensics and legal support.
An area that may not be covered is an employee taking your proprietary trade secrets to a competitor. The loss of value of your company due to your trade secrets becoming publicly known will not be covered by insurance.
Acquiring an appropriate cyber insurance policy that will cover you for unforeseen incidents, along with strong controls, will ensure your data stays where it belongs: with your company.
Author
Table of Contents










