Blog
Public Company CISOs Beware: The SEC Is No Longer Playing Nice
On October 30, the US Securities and Exchange Commission (SEC) announced fraud charges against SolarWinds and its former chief information security officer (CISO), alleging that “SolarWinds’ public statements about its cybersecurity practices and risks were at odds with its internal assessments.” This comes on the heels of the SEC’s newly implemented rules for disclosures relating to cyber risk. Publicly traded companies (along with pre-IPO and foreign private issuers) must now adhere to new and prescriptive rules requiring the disclosure of “material cybersecurity incidents” as well as annual disclosures relating to “cybersecurity risk management, strategy, and governance.”

There is a lot going on with all the recent SEC and cyber headlines, so let’s break it down piece by piece. This blog outlines several high-level calls to action that CISOs and stakeholders should consider as they work through their cyber risk strategy and their cyber and/or D&O insurance renewals.
|
Also read: |
The First Step: Implement Cybersecurity Controls
Let’s dive into some cyber risk management controls that, as a CISO, you should be implementing (or actively lobbying for) in your organization—because the SEC and other relevant third-party claimants are more likely to go after you and your company when a very public, catastrophic, and expensive cyberattack happens.
- Have an incident response plan, a business continuity plan, and a disaster recovery plan. Make sure it addresses your company’s cyber risks and test it at least annually.
- Have a comprehensive understanding of your network topography, where your assets are, how critical they are, and how to restore and reconstruct your network in the event of an Armageddon scenario.
- Implement basic ransomware preparedness controls:
a. Ensure multifactor authentication for remote access, cloud applications including email, and privileged/administrative accounts.
b. Make sure your backups are segmented, immutable (or otherwise uncorruptible), properly secured with separate credentials, and tested frequently. Make sure you also have backups on configurations for network infrastructure and telephony systems.
c. Have an endpoint detection and response (EDR) solution in place with 24x7x365 monitoring with logging and quarantine capabilities.
d. Implement a strict patching cadence of +/- 7 days for high and critical vulnerabilities.
e. Train your employees to recognize suspicious communications and to never open attachments from unknown senders.
4. Undertake a data discovery audit. Know where sensitive data sits and how it is protected. A large percentage of data breaches occur because an old database with countless highly sensitive data points went undiscovered (and unsecured) until the bad guys found it.
Not There Yet? Don’t Panic
If your company isn’t at an “ideal” stage of cyber preparedness or maturity, don’t panic. Every journey begins with a single step and you and your team probably have access to resources you may not have thought of. For example, some companies may already have a foundational cyber risk management strategy by virtue of their engagements with cyber insurers, brokers, privacy attorneys, technology consultants, and service providers. If your company has attempted to or currently carries cyber liability insurance, you have already worked to put together detailed information around your incident response plans, disaster recovery, and data protection strategies.
For companies truly beginning from ground zero, the changes in cyber security risk management strategy will likely be a paradigm shift for the entire enterprise, including board members and your C-suite peers. This means the group working on this must open new lines of communication and learn new languages. Fundamentally, clear and open lines of communication and establishing trust and accountability for all stakeholders will be key drivers of success.
Get Guidance in Building Your Risk Management Strategy
Since the wholesale construction of a company’s cyber risk management strategy requires the involvement of many disciplines (not least of which is privacy), seek support from your company’s securities attorneys, privacy counsel, insurance brokers and carriers, and any other experts to advise your team as you go through your dirty laundry. We strongly advise you to engage outside counsel to establish attorney-client privilege at the onset of this journey. Having outside counsel involved may help to protect you and your team as you prioritize projects and make decisions on risk management initiatives—while also justifying your methodologies and timelines in writing. (Where did we see before?)
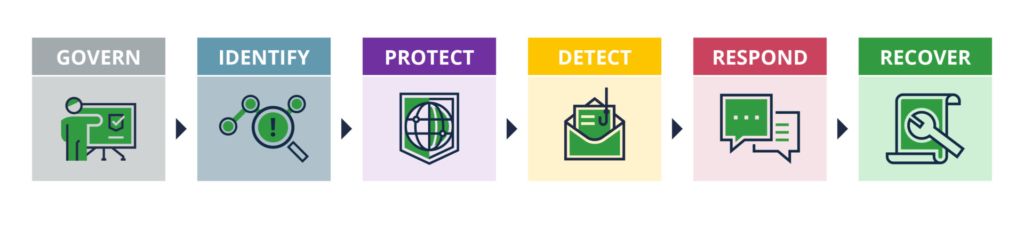
A tried-and-true starting point to build a roadmap for holistic cybersecurity governance for any company may be the NIST Cybersecurity Framework. The process flows in a logical method and plots a high-level path for boards, audit committees, and management to begin mapping their organization’s cyber risk:
What Does D&O Insurance Cover?
Finally, there is a lot of uncertainty and angst around the intersection of cyber and D&O insurance coverage—specifically in the context of the two policies’ potential coverage for the recent SEC claim against SolarWinds and its former CISO. To be clear, D&O policies should respond to claims alleging mismanagement of a company by its directors and officers and act as an effective backstop and protection for personal assets. This means a D&O policy should respond to the SolarWinds claim resulting from the SEC's October 30 fraud charge. Furthermore, a typical cyber policy would not respond to this type of claim because they are built to respond to loss or theft of data and any resulting privacy litigation.
Let’s shed some light on coverage questions and few calls to action for CISOs to protect themselves:
- Get clarity around your company’s D&O coverage. Why? Because the policy may not consider your specific title as an insured person or may carry an overly broad cyber exclusion, which means you're not covered in the event of a lawsuit.
- Ensure your organization is providing proper indemnification. CISOs and their functional equivalents can be held personally liable for actions impacting their company and defending these claims can be horrifically expensive. Make sure you have an indemnification agreement in place with your company to help protect your personal assets in the event of a third-party suit.
- Be deliberate in understanding both your D&O and cyber coverage at renewal. Make sure your cyber broker is aware of what is and is not covered in the D&O coverage so there are no gaps, and vice versa. Coverage gaps are resolvable, but it takes some focused tinkering and negotiating with your insurers—your broker needs to be doing this on your behalf.
Align Your D&O and Cyber Coverage
Regardless of how prepared your company is to meet these SEC requirements today, aligning your cyber and D&O insurance brokers is a great way to simplify efforts and prepare to meet this challenge head-on (and not alone). Working together, your brokers can help you:
- Create efficiencies in underwriting data collection and insurance renewal efforts.
- Support your team with the alignment of company cyber risk management objectives.
- Bring clarity to how your management liability and cyber policies respond to cyber-related claims.
- Leverage your insurance providers to support risk management initiatives, including subsidizing the costs for cyber incident table-top exercises, privacy policy audits, or network interruption preparedness.
- Provide your board and management with objective, actionable, and data-driven advice around D&O and cyber insurance purchasing strategies.
It might be a scary time to be a CISO, but knowing the steps to take to protect your company from cyberattacks—and protect yourself from liability—is your best defense. Reach out to your broker to learn how you can beef up your cybersecurity controls and ensure you have the protection you need.
Author
Table of Contents










