Blog
What Is Remote Desktop Protocol and Why Is it a Cyber Risk?
This article is part of a series for National Cyber Security Awareness Month in October. Woodruff Sawyer is proud to be recognized as a champion of cybersecurity by the National Cybersecurity Alliance for the third consecutive year in 2020.
Remote desktop protocol is an important function for companies that want to offer employees access to systems remotely. But it’s a growing cyber risk, as bad actors increasingly exploit it to install ransomware. Here, we’ll discuss what remote desktop protocol is, the risks, and how to mitigate those risks–– including cyber liability insurance.
What Is Remote Desktop Protocol?
Remote desktop protocol is a Microsoft Windows interface that allows a user to connect through the internet with another computer or server and all the tools and software installed on it. As RDP is a Windows interface, you can only establish remote connections with Windows PCs and Windows Server.
Why do companies use it? To enable remote access to a Windows machine. Here are a couple of common scenarios today:
- An IT department is no longer able to perform work on an employee laptop in person since everyone is working remotely due to the pandemic.
- The network drives suffer a malfunction, and the servers that support the drives need to be accessed and patched in order to bring the drives back online.
In both of these scenarios, RDP allows your IT department to access these systems as if they were in the office, without having to be physically present.
Because Microsoft Windows is the dominant operating system globally, RDP is widely used. But enabling RDP can also provide an open door for bad actors looking to attack your company, particularly if access to the RDP ports is open to the public internet.
After all, the user with remote access has full reign over the system as if they were physically in front of the computer, whether that user is your IT department staff or a bad actor.
The Link Between RDP and Ransomware Attacks
Increasingly, bad actors use open RDP ports to access an organization’s systems and install ransomware. Ransomware is a type of malware that encrypts, and often steals, an organization’s data, threatening to release the data or block access until the victim pays a ransom.
There has been a marked increase in remote desktop protocol attacks over the past quarter, according to Coveware Quarterly Ransomware Report, Q2 2020.
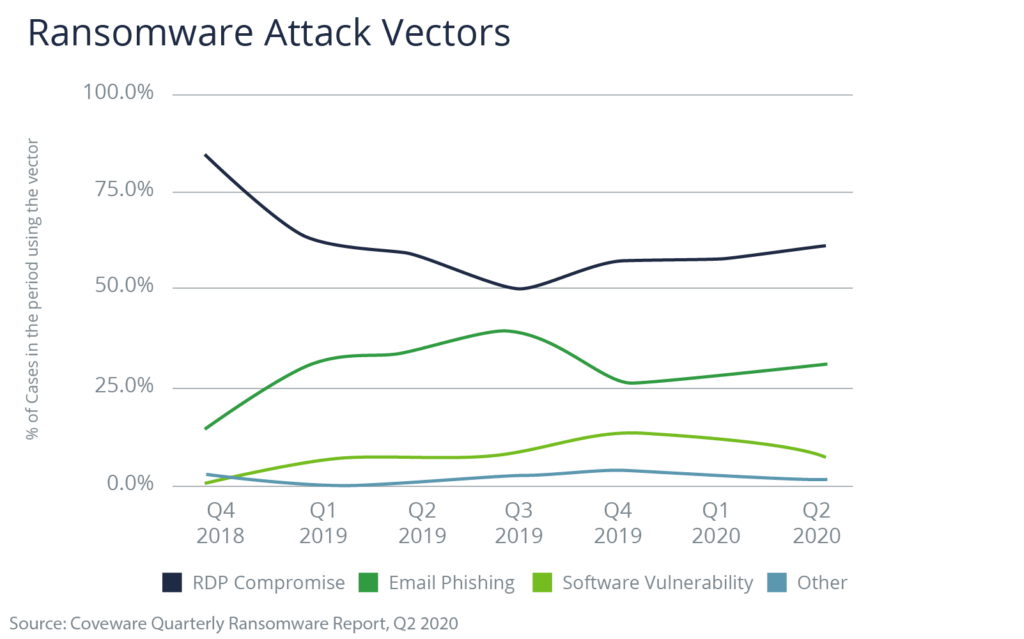
Kaspersky data supports this, showing that brute force RDP attacks have been on the rise. Brute force attacks systematically try all username and passwords combinations until one is found that works.
A key contributor to the uptick in RDP attacks is the migration of employees from the workplace to the home environment due to the pandemic. Early reports showed that RDP usage was up 41% since the onset of the pandemic as companies enabled remote work.
I’ve discussed previously the cyber risks that a remote workforce is presenting right now, not the least of which is employees working from unsecure networks--such as a home internet connection, which is not password protected, or a public internet connection like at coffee shops, airports, and hotels.
While ransomware attacks that compromise the RDP more frequently target smaller companies, large enterprises are not immune. According to Coveware data, nearly 40% of ransomware cases for large companies use the RDP attack vector.
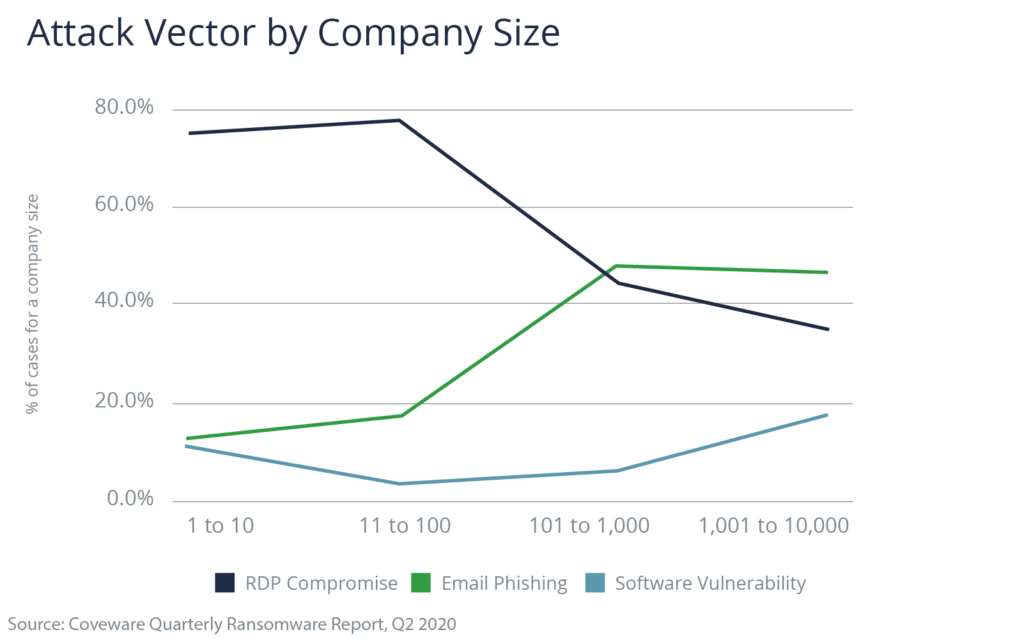
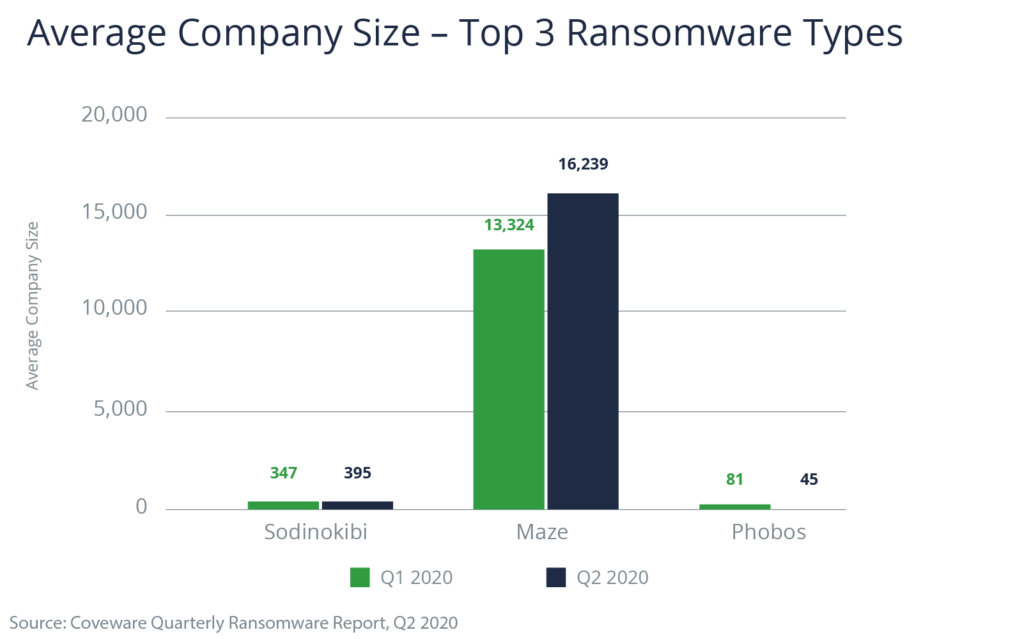
Maze, for example, is a strain of ransomware that typically targets larger companies:
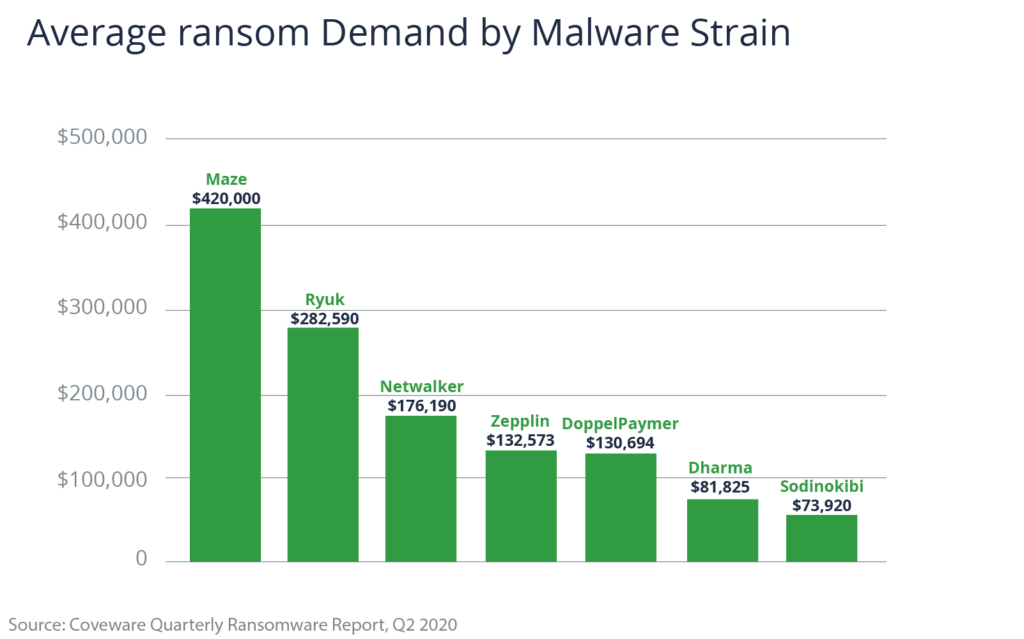
And, according to Coalition’s H1 2020 Cyber Insurance Claims Report, it’s Maze that commands the largest ransom:
Best Practices for Securing Remote Access
For many companies, working from home is now the new norm and remote access to a company’s systems is not going away. Securing remote access is relatively easy. Consider the following best practices:
- Disable RDP if your company does not use it or doesn’t need it. Ask: Is remote access truly required at your company?
- If you need RDP, limit it to a specified set of individuals or IP addresses that can access the RDP port. You can close unused ports after completing a task or project, too.
- Alternatively, use a Virtual Private Network (VPN) with multi-factor authentication (MFA). Microsoft states that MFA can block over 99.9 percent of account compromise attacks. Remember, though, that you may lose some functionality when using a VPN versus an RDP.
- Make sure you’re using the most current version of Windows and update and patch regularly.
- Ensure you have strong password policies in place and change passwords often. Remember, length of passwords is as important as complexity.
- Change the standard port which has RDP enabled. By default, Windows servers use port 3389 for RDP and many attackers scan the internet for this specific port when looking for easy targets. By changing the standard RDP port, you won’t stop a determined attacker but you may not be included on a list of easy targets when attackers search for the standard port 3389.
How Cyber Insurance Is Responding to RDP Attacks
Cyber insurance policies are designed to respond to things like ransomware attacks via RDP ports. But because of the increasing frequency and severity of these attacks (where insurers are paying the ransom), the insurance underwriting requirements are getting tighter.
Expect to provide more details than ever before about practices and controls when placing or renewing your cyber policy. Underwriters want to understand the risk they are ensuring, and often have access to network scanning tools that can identify open RDP ports prior to offering coverage.
As vulnerabilities in remote access to your systems are discovered, insurers will want to know how they are being addressed and why you have a need for an open RDP port. Deploying some of the best practices noted above can ensure a more favorable quote for insurance.
And if you have been hit with ransomware via an RDP attack, there are a number of steps you’ll want to take to set yourself up for success during a claim, which have been outlined here in this action plan for ransomware attacks.
At the end of the day, securing your network from RDP vulnerabilities is a best practice that can keep your company from appearing on the long list of ransomware victims.
Author
Table of Contents










