Blog
Malware Attack Readiness: Is Your Organization Prepared for a Ransomware Attack?
Directors have a lot of cyber issues to be concerned about. One of the most pernicious—but addressable—cyber threats out there is ransomware. These malware attacks can be surprisingly sophisticated.. It's a good idea to ask your management team what steps they have taken to prepare for a ransomware event.
Ransomware is a type of malware that gets installed on a device, encrypts files, and gives criminals control of your files. Cybercriminals use ransomware as a way to extort money from an organization. After taking control of critical files, the criminals extort ransom by holding the files hostage—and threatening to possibly delete or corrupt the files—unless the ransom is paid.
This type of malware is on the rise. The FBI reported a spike in ransomware incidents starting in 2015. According to Business Insider reports, ransomware victims paid a total of $24 million to cyber criminals that year.
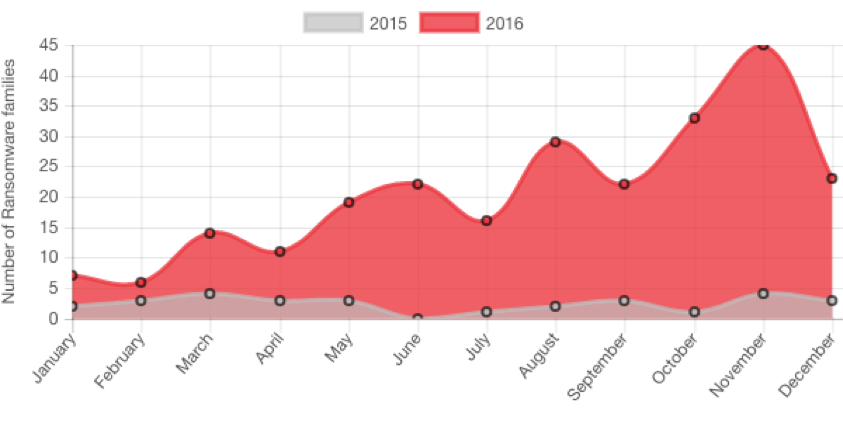
In 2016, reports surfaced that cyber criminals collected $209 million in the first three months of the year. In fact, one report shows ransomware spiked 752% last year:
Phishing scams are often a precursor to ransomware. A person in an organization might receive a phishing email, for example, and click on an infected link that installs the malware.
That's not the only way in, however. Ransomware attacks are becoming more sophisticated. According to an article at FBI.gov:
And in newly identified instances of ransomware, some cyber criminals aren't using e-mails at all. According to FBI Cyber Division Assistant Director James Trainor, "These criminals have evolved over time and now bypass the need for an individual to click on a link. They do this by seeding legitimate websites with malicious code, taking advantage of unpatched software on end-user computers."
A recent public service announcement from the FBI on ransomware provides more information, including the fact that paid ransom may not unlock files:
Recent variants have targeted and compromised vulnerable business servers (rather than individual users) to identify and target hosts, thereby multiplying the number of potential infected servers and devices on a network. Actors engaging in this targeting strategy are also charging ransoms based on the number of host (or servers) infected. Additionally, recent victims who have been infected with these types of ransomware variants have not been provided the decryption keys for all their files after paying the ransom, and some have been extorted for even more money after payment.
These attacks can happen to any type of organization or sector. You may have been aware of the 2016 case in the Bay Area involving an attack on the San Francisco Municipal Transportation Agency (Muni), when it was infected with ransomware that took down the ticketing system, resulting in free rides for patrons and ultimately, a loss of revenue.
Ransomware scenarios can range from not that interesting to severe, including, according to the FBI, things like "loss of sensitive or proprietary information, the disruption to regular operations, financial losses incurred to restore systems and files, and the potential harm to an organization’s reputation."
In 2016, the FBI issued guidance on reporting ransomware cases to the agency in a public service announcement (linked to earlier), recognizing that "victims may not report to law enforcement for a number of reasons, including concerns over not knowing where and to whom to report; not feeling their loss warrants law enforcement attention; concerns over privacy, business reputation, or regulatory data breach reporting requirements; or embarrassment."
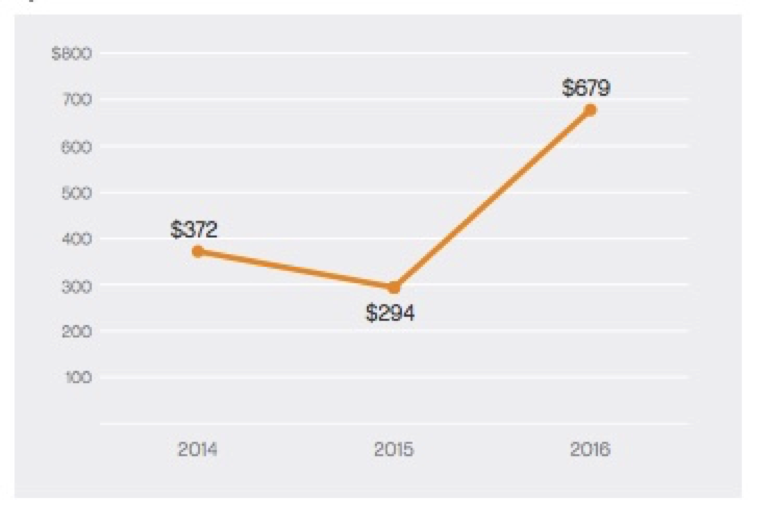
It's true that organizations often don’t report ransomware incidents because the requests for payment are relatively low (Symantec reports the average ransom was $679 in 2016; the range is obviously broad), and the biggest issue is usually figuring out how to get bitcoin to pay the ransom.
However, the agency urges organizations to report, because these reports allow the FBI to:
- Gain a greater understanding of the threat.
- Provide justification for ransomware investigations.
- Contribute relevant information to ongoing ransomware cases.
- Determine who is behind the attacks, and how they are identifying or targeting victims.
However, if faced with an incident, it's a good idea to first talk to your own lawyers to determine the appropriate manner to proceed, including whether or not you contact the FBI at all.
If the stakes are high, should you pay the ransom? The FBI's official stance on ransomware is to not pay cybercriminals anything when faced with an incident.
The agency reiterated that in some cases, it may not resolve the situation, and that "paying a ransom emboldens the adversary to target other victims for profit, and could provide incentive for other criminals to engage in similar illicit activities for financial gain."
But the FBI also recognizes the decisions that executives must make when faced with a ransomware incident:
While the FBI does not support paying a ransom, it recognizes executives, when faced with inoperability issues, will evaluate all options to protect their shareholders, employees, and customers.
Of course, as part of a company's internal cyber risk management, you'll want to proactively assess the vulnerability to ransomware activity and take all appropriate steps to repel. The FBI offers several tips when it comes to preventing ransomware that are worth checking out at the article linked to earlier.
Finally, consider insurance as a risk transfer opportunity. Happily, ransomware is a peril that can be covered by insurance.
This is a peril that a well-negotiated cyber liability insurance policy will cover. Part of the benefit of having this addressed by your insurance policy is that many carriers have effective resources they can deploy on your behalf in a ransomware situation, in addition to providing a financial response. Finally, some "special risk" policies (also known as "kidnap and ransom"policies) may also provide coverage for ransomware events.
Author
Table of Contents