Blog
Coronavirus Impact on Cyber Insurance Coverage
This blog post can also be found on our Coronavirus Resource Center.
Cyber risk has been cited as a top risk for organizations over the next 20 years due to the growing reliance on technology and the increasing sophistication of cyber attackers. As the COVID-19 pandemic has reshaped the corporate landscape, many companies are realizing that cyber risks over the next 20 years have arrived at their doors in the last two weeks.

Many companies have moved to an entirely remote workforce as shelter-in-place guidelines have been enforced across state and local governments alike. Cyber attackers, in all their ingenuity, have taken advantage of the coronavirus to deploy their malware and take advantage of the newly remote workforce. Recently, the World Health Organization was the target of attacks and the FBI issued a warning of increased fraud schemes related to the pandemic.
Fortunately, the insurance industry has been preparing for the cyber risks of the future and a modern cyber insurance policy can address the very risks that have risen to the top of mind for many companies today: operational and security risk.
Three Types of Cyber Risk
Cyber risk can be broken down into three main types of risk: security risk, privacy risk, and operational risk.
Security risk is as the name suggests: the risk of a security incident causing damage to an organization. The risk most commonly associated with cyber risk, this risk can take the form of a data breach, a successful phishing attempt, or a malware attack. The impact from a security incident can be felt both monetarily as well as reputationally.
Privacy risk is related to regulations and contractual indemnities that surround the privacy rights of your consumers or other entities with whom you contract. Privacy legislation now defines consumer rights with regard to the collection, processing, storage, and use of data through laws such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act of 2018 (CCPA). Additionally, more companies are implementing contractual controls to protect their interests with regards to privacy. Many business-to-business contracts now require indemnification for the damages associated with a data breach.
Operational risk lies in a reliance on technology. This dependence on technology for providing services and generating revenue creates a risk to the business in the event of a hack or cyber business disruption. If, for example, a certain mission-critical technology is not available when needed or access to your network is impaired, you may face financial losses due to the interruption of your business activities.
It's important to note that there may be an overlap between the three main types of cyber risk. After all, a security incident may highlight security risks in an organization and ultimately lead to privacy or operational risks. However, together these three main cyber risks provide a framework to consider how cyber insurance can support a company in transferring risk to an insurance carrier.
Insuring Operational Cyber Risk
With the reality of a remote workforce setting in for numerous companies as the virus spreads, many companies now recognize the operational risk that impacts their company. When all employees are remote and rely on technology to connect, communicate, and perform their job functions, companies will find themselves more reliant on technology than ever.
This reliance on technology increases risk for most organizations, but there are options to transfer this operational risk to an insurance carrier through a dedicated cyber insurance policy.
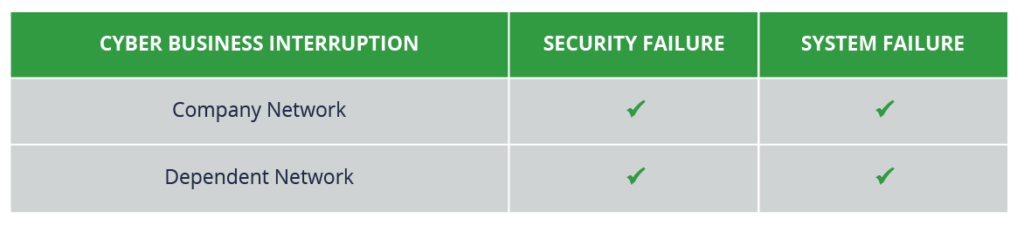
Typically, a cyber business interruption insuring agreement will respond to an operational risk event. When assessing coverage for cyber business interruption there are four key components that should be included in your policy.
You can think of it like a matrix: two different event types at two different levels.
The event types you need present in your policy are security failures and system failures.
The two levels in which they need to be covered are an event on your own network, and an event on a dependent network—the network of a key supplier or vendor of services to you.
Security Failure
The security failure event coverage is triggered by the failure to secure a computer system or network. This often results in the transmission of malware, denial of service attacks, unauthorized access or use of the network, damage to a digital asset, or the prevention of authorized, legitimate access to the network, among other digital maladies.
The most common security failure event that leads to business interruption claims recently is ransomware. In this attack, attackers will encrypt access to your network drives and data, then offer to restore it for a fee, or "ransom."
System Failure
The system failure event coverage is triggered by an unintentional or unplanned network outage which is not caused by a security failure. This is a purposely broad range of potential events. Computer systems and networks tend to fail, even without an attacker targeting that network.
System failures can be the result of a hardware failure, a failed patch or software upgrade, or even a human error event.
Notably, given the challenges of transitioning to a remote workforce, we have seen an increase in inquiries regarding claims for a slowdown in business due to challenges in getting employees remote setups configured correctly. There are two key issues to highlight here:
- First, business interruption coverage often does respond to a partial impairment of a computer network. The network does not need to be completely unavailable in order to trigger coverage.
- Second, the loss suffered must be demonstrably the result of the network impairment, as opposed to being the result of other economic factors.
Given the broad negative impact of coronavirus on the global economy, proving a loss of business income is related to a network slowdown is the result of remote employees and not the general conditions of the economy will be difficult.
Key Definitions and Exclusions to Study Closely
As with all insurance policies, once you clear the burden of triggering coverage under the policy, you then need to consider any relevant definitions or exclusions. There's an old saying in the insurance community regarding drafting policy language: If an insurance carrier really wanted to exclude coverage on a tricky issue, they certainly wouldn't do so in the exclusion section.
Rather, they will craft very specific definitions to key coverage items in the definitions section of the policy, often limiting coverage through how a term is defined.
As it relates to coverage for business interruption, which is exacerbated by the new realities of remote working, there are a few key definitions and exclusions to pay close attention to in your cyber policy.
Computer System Definition
Most cyber insurance policies define what constitutes an insured company's computer system in the policy form. Typically, the definition includes computer software and hardware, including any data thereon, owned, operated or leased by the insured organization.
The key piece of the common definition above is the requirement that hardware and software is "owned, operated or leased by" the company. This definition should be reviewed to ensure an employee working on a personal computer at home is covered.
Voluntary Shutdown Coverage
When a company finds themselves the target of a malware attack, a natural instinct is to voluntarily shutdown their computer network to prevent further damage. However, this action may preclude coverage if the voluntary shutdown is not part of advice from an approved IT forensics consultant or the policy language is not amended.
Many cyber insurance carriers will provide coverage for a voluntary shutdown, but it must be negotiated into the policy wording in advance of an event occurring.
Infrastructure Exclusion
Cyber insurance policies typically exclude any network outages which are the result of a failure of infrastructure services not under the direct operational control of the insured company, such as power, utilities, or internet service providers.
In the context of remote working, this exclusion is key when considering an employee losing internet access at their home or having a slower connection than what is available at the company offices.
Coronavirus has changed how nearly every company operates and exacerbated security and operational cyber risk. Cyber insurance is now a key cog in a modern company's insurance portfolio, which can specifically address and mitigate these increased risks.
Author
Table of Contents